

Customer stories Case: AI Security Agent
We developed an AI agent that never sleeps – it monitors cybersecurity feeds around the clock, detects threats, and reports them automatically!
Cybersecurity threats are constantly emerging. New vulnerabilities are published across various sources every day, and identifying what’s relevant requires expert judgment. In many organizations, this means manual monitoring and sifting through large amounts of information—creating the risk that something important might be missed or reactions delayed.
At Hurja, we wanted to improve the process of monitoring cybersecurity sources and identifying relevant findings. AI proved to be a good fit for the task, as it combines efficiency with the ability to understand context. We organized an internal AI hackathon* with the goal of exploring how the manual process of detecting security risks could be automated using large language models (LLMs) and agent-based architecture.
The goal was to build an intelligent solution that monitors multiple cybersecurity sources, identifies relevant threats, and reports the findings in a clear and understandable way – reducing the time experts need to spend on daily manual screening.
*A hackathon is an intensive, short-term development event where a team builds new solutions within a limited time frame.
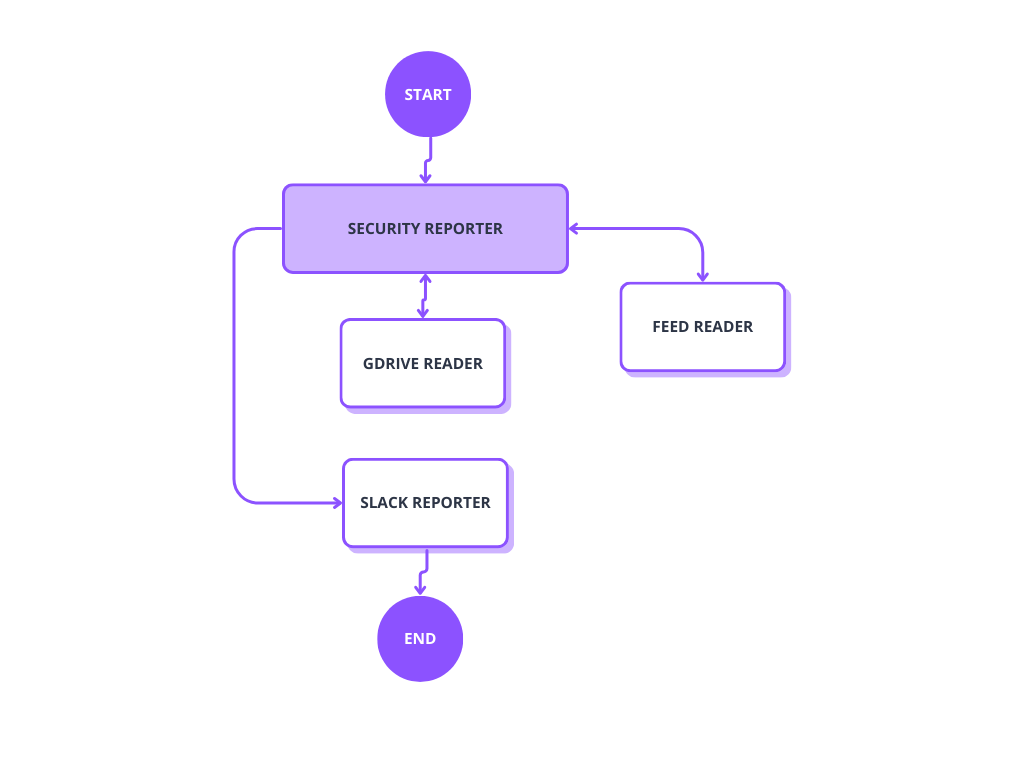
During the hackathon, we developed an AI solution that monitors trusted cybersecurity sources and automatically reports relevant findings to the necessary communication channels. In the solution we built, users can define which technologies and keywords to monitor—and on what criteria—without writing a single line of code.
The agent is built using the LangChain and LangGraph frameworks, allowing it to process data step by step: read the inputs, identify what’s relevant, and summarize the findings. LangGraph enables the agent to understand where it is in the process, what it has already handled, and what still needs to be reviewed.
The agent’s behavior is guided by instructions written in natural language—known as prompts. When requirements change, there’s no need for new programming—updating the prompt is enough.
The core of the AI agent architecture:
This type of architecture is a great fit for a variety of use cases, including:
The greatest benefit of the solution is its ability to process large amounts of data consistently and quickly. The AI agent reduces the manual effort required for monitoring security sources at Hurja, and supports our experts by helping them focus on action instead of early-stage filtering.
The agent automatically generates summaries and highlights relevant items, which makes it possible to respond more quickly—and deal with potential threats before they become real issues.
The solution is also easy to implement and adapt for different needs. The same technical structure can be applied to many other use cases, such as analyzing customer feedback or monitoring publicly available data sources.
Key benefits:
AI agents like this open up entirely new ways to automate data collection and decision-making. They’re flexible, customizable, and fast to deploy—exactly what modern organizations need.
If your organization works with data, makes decisions, and needs to respond quickly—we know how to put AI to work for you.
Let’s build your own AI agent that takes care of the routine—so people can focus on smarter decisions.